Understanding the Domain Name System (DNS) in the Application Layer
The Domain Name System (DNS) is one of the most crucial components of the internet’s application layer. It acts as a directory service, translating human-readable domain names (like www.example.com) into machine-readable IP addresses (like 192.0.2.1). Without DNS, users would need to memorize complex numerical IP addresses to access websites, making the internet far less user-friendly.
What is DNS?
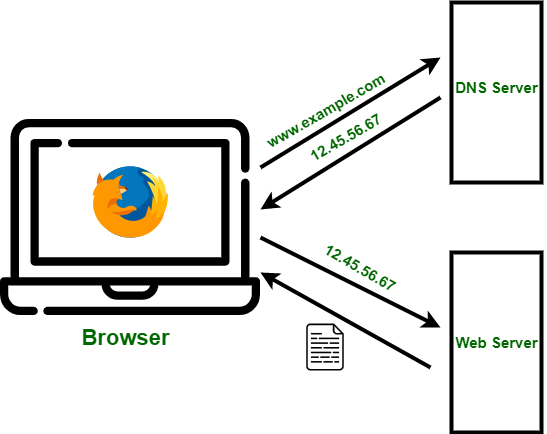
DNS is a distributed naming system that allows users to access websites and services with easy-to-remember domain names instead of numerical IP addresses. It functions as a hierarchical system where the DNS server resolves domain names into IP addresses, allowing users to connect to websites, email servers, and other online services.
For example, when a user types “www.example.com” into a web browser, DNS servers convert this domain name into an IP address (e.g., 192.0.2.1), allowing the browser to establish a connection to the appropriate web server.
Key Components of DNS:
- Domain Names: The domain name represents a human-readable address for websites, services, or devices on the internet.
- Example: www.example.com, mail.google.com.
- DNS Resolver: A DNS resolver is responsible for initiating and processing the queries to convert domain names into IP addresses. The DNS resolver can be provided by an Internet Service Provider (ISP) or configured manually by the user.
- DNS Server: The DNS server contains databases of records that map domain names to IP addresses. There are different types of DNS servers:
- Authoritative DNS Server: Provides answers to queries for domains within its zone of authority.
- Recursive DNS Server: Handles queries from clients by contacting other DNS servers until it finds the correct IP address.
- DNS Records: These records store the information related to domain names, such as:
- A Record: Maps a domain name to an IPv4 address.
- AAAA Record: Maps a domain name to an IPv6 address.
- MX Record: Specifies the mail server for a domain.
- CNAME Record: Used to alias one domain name to another.
How Does DNS Work?
DNS operates in a client-server model. When a user attempts to access a domain, the following process occurs:
- Query Initiation: The user types a domain name into the browser (e.g., www.example.com).
- DNS Resolver: The query is first sent to a DNS resolver, which checks if it has the corresponding IP address in its cache.
- Iterative Search: If the IP address is not cached, the DNS resolver contacts a series of DNS servers:
- Root DNS Server: The resolver first queries the root DNS server, which directs the resolver to the appropriate TLD (Top-Level Domain) server (e.g., .com, .org).
- TLD DNS Server: The TLD server provides the address of the authoritative DNS server for the domain.
- Authoritative DNS Server: The authoritative DNS server returns the IP address of the requested domain.
- Response: The DNS resolver sends the IP address back to the user’s browser, allowing the website to load.
Importance of DNS
DNS is a fundamental part of internet infrastructure. Without it, the web would be difficult to navigate, as users would need to remember the numerical IP addresses of every website they visit. DNS simplifies the internet experience by providing an easy-to-use naming system.
In addition to its primary function of name resolution, DNS is also essential for email routing, network services, and security, such as DNSSEC (DNS Security Extensions) to prevent attacks like DNS spoofing.
DNS Caching
To improve performance and reduce the load on DNS servers, DNS responses are often cached. This means that once a domain name is resolved, the DNS resolver stores the IP address in its cache for a certain period, known as the Time To Live (TTL). This allows subsequent requests to be answered more quickly.
Common DNS Issues
- DNS Spoofing: Attackers can exploit DNS vulnerabilities to redirect users to malicious websites. This is why DNS security is essential.
- DNS Propagation: Changes made to DNS records can take time to propagate across the internet, meaning users may not immediately see the updated records.
- DNS Server Failures: If a DNS server goes down, users may not be able to access websites associated with that server.
[doc id=24694]
2 Mark Questions:
- What is DNS?
- DNS (Domain Name System) is a system that translates human-readable domain names (like www.example.com) into machine-readable IP addresses (like 192.0.2.1). It acts as a directory service, making it possible for users to access websites using easy-to-remember names instead of numerical IP addresses.
- Explain the role of DNS in the Application Layer.
- DNS operates at the application layer of the OSI model. Its primary role is to enable the translation of human-readable domain names to IP addresses, facilitating communication between users and servers. Without DNS, users would need to remember IP addresses to access websites, making the internet less user-friendly.
- List any two types of DNS records and explain their functions.
- A Record (Address Record): Maps a domain name to an IPv4 address, allowing users to reach a website using its domain name.
- MX Record (Mail Exchange Record): Specifies the mail server for a domain, guiding the delivery of email messages.
- What is the function of a DNS resolver?
- A DNS resolver is responsible for querying DNS servers to translate domain names into IP addresses. It is usually provided by an Internet Service Provider (ISP) and handles the recursive resolution process, starting from the root server to the authoritative DNS server.
- What is the purpose of caching in DNS?
- Caching in DNS is used to store previously resolved domain name queries in memory for a specified duration (TTL – Time To Live). It speeds up the resolution process by allowing repeat queries to be answered faster and reduces the load on DNS servers.
5 Mark Questions:
- Explain the working of DNS with a flow diagram.
- The DNS resolution process typically follows these steps:
- The user enters a domain name (e.g., www.example.com) in the browser.
- The request is sent to the DNS resolver.
- If the resolver does not have the IP address cached, it sends the query to a root DNS server.
- The root server directs the resolver to a TLD (Top-Level Domain) server (e.g., for .com).
- The TLD server directs the resolver to the authoritative DNS server for the domain.
- The authoritative DNS server returns the IP address for the domain.
- The resolver sends the IP address to the user’s browser, allowing the website to load.
- User → DNS Resolver → Root DNS Server → TLD DNS Server → Authoritative DNS Server → IP Address → User’s Browser
- The DNS resolution process typically follows these steps:
- Describe the steps involved in domain name resolution.
- Step 1: The user types a domain name in the browser (e.g., www.example.com).
- Step 2: The browser queries the DNS resolver to resolve the domain name.
- Step 3: The DNS resolver checks its cache. If the record is not cached, it sends a request to the root DNS server.
- Step 4: The root server directs the resolver to the TLD server for the domain (.com, .org, etc.).
- Step 5: The TLD server directs the resolver to the authoritative DNS server for the domain.
- Step 6: The authoritative DNS server returns the IP address for the domain.
- Step 7: The DNS resolver sends the IP address to the browser, which connects to the web server to load the website.
- Differentiate between authoritative and recursive DNS servers.
- Authoritative DNS Server: An authoritative DNS server contains the actual DNS records for a domain. It is the final source for resolving domain names into IP addresses.
- Recursive DNS Server: A recursive DNS server does not store DNS records. Instead, it queries other DNS servers (root, TLD, authoritative) to resolve a domain name and provides the final result to the user.
- What is DNSSEC? How does it help in securing DNS?
- DNSSEC (Domain Name System Security Extensions) is a set of security protocols that add digital signatures to DNS data. It ensures the authenticity and integrity of DNS responses, protecting against attacks like DNS spoofing or cache poisoning. DNSSEC verifies that the data received by a DNS resolver has not been tampered with during transmission.
- Discuss the different types of DNS records used in DNS and their functions.
- A Record (Address Record): Maps a domain to an IPv4 address, allowing browsers to connect to the correct web server.
- MX Record (Mail Exchange Record): Specifies the mail server responsible for receiving emails for a domain.
- CNAME Record (Canonical Name Record): Allows one domain to alias another (e.g., blog.example.com → www.example.com).
- NS Record (Name Server Record): Specifies the authoritative DNS servers for a domain.
- AAAA Record: Maps a domain to an IPv6 address.
- Describe how DNS resolves a domain name into an IP address.
- When a user requests a domain name, the DNS resolver starts the resolution process by checking its cache. If the domain is not cached, the resolver queries the root server, then the TLD server, and finally the authoritative server. The authoritative server returns the IP address, which is sent back to the browser, allowing it to connect to the web server.
10 Mark Questions:
- Explain the process of DNS resolution in detail, including all steps and types of DNS servers involved.
- The DNS resolution process begins when a user types a domain name into a browser. The browser sends a request to the DNS resolver. If the resolver has the domain cached, it returns the IP address immediately. If not, it initiates a recursive query:
- DNS Resolver: Queries the root DNS server.
- Root DNS Server: Directs the resolver to the appropriate TLD server (for example, .com or .org).
- TLD DNS Server: Points the resolver to the authoritative DNS server for the domain.
- Authoritative DNS Server: Provides the IP address for the domain.
- The IP address is sent back to the browser, which establishes a connection to the web server. The entire process typically occurs in milliseconds, ensuring seamless access to websites.
- The DNS resolution process begins when a user types a domain name into a browser. The browser sends a request to the DNS resolver. If the resolver has the domain cached, it returns the IP address immediately. If not, it initiates a recursive query:
- What are the security challenges in DNS? Discuss DNS spoofing and how DNSSEC mitigates such attacks.
- DNS Spoofing (Cache Poisoning): In this attack, an attacker injects fraudulent DNS records into a DNS resolver’s cache, redirecting users to malicious websites. This can be used to steal sensitive information like passwords or inject malware.
- DNSSEC: DNSSEC helps mitigate such attacks by adding digital signatures to DNS responses. This allows DNS resolvers to verify the authenticity of the data they receive. If the DNS record is tampered with, the resolver will detect the invalid signature and reject the data, ensuring the user is directed to the correct website.
- Describe the structure of the Domain Name System. How does DNS make the internet user-friendly?
- DNS is a hierarchical, distributed system:
- Root DNS Servers: The top of the hierarchy, pointing to TLD servers.
- TLD DNS Servers: Direct queries to authoritative servers.
- Authoritative DNS Servers: Hold the actual DNS records for specific domains. DNS makes the internet user-friendly by allowing humans to use easily memorable domain names (like www.google.com) instead of IP addresses. This simplifies the user experience and enables people to access websites and services easily.
- DNS is a hierarchical, distributed system:
- Explain the concept of DNS caching. What are the advantages and potential issues associated with caching in DNS?
- DNS Caching: In DNS caching, DNS resolvers store previously resolved domain name queries for a specified period (TTL). This reduces lookup times and decreases the load on DNS servers.
- Advantages:
- Improved Performance: Subsequent requests for the same domain are resolved faster because the IP address is cached.
- Reduced Traffic: Less frequent querying of authoritative servers reduces network load.
- Potential Issues:
- Stale Data: Cached records may become outdated, causing users to be directed to incorrect or old IP addresses.
- Cache Poisoning: If malicious data is cached, users could be redirected to harmful websites, although DNSSEC helps mitigate this risk.
15 Mark Questions:
1. Discuss the importance of DNS in the internet infrastructure. How does it enable the seamless operation of the web? Include a detailed explanation of the DNS hierarchy, types of DNS servers, and records.
Importance of DNS in Internet Infrastructure
The Domain Name System (DNS) is a fundamental pillar of the modern internet, acting as the “phonebook” of the internet. It enables users to access websites using human-readable domain names (e.g., www.google.com) instead of numerical IP addresses (e.g., 192.168.1.1), which are difficult to memorize. DNS allows users and devices to navigate the vast expanse of the internet effortlessly.
Role in Seamless Web Operation:
- User-Friendly Navigation: DNS makes browsing easy. Without DNS, users would have to remember complex IP addresses to access websites, which is impractical. With DNS, users simply type in a domain name (like www.example.com), and DNS resolves it into the corresponding IP address.
- Distributed System: The DNS is a distributed and hierarchical system, meaning that no single entity controls the entire system. This decentralized nature ensures that DNS can scale to handle billions of queries every day without major disruptions.
- Email Routing: DNS is not just for websites. It also helps route emails by using MX (Mail Exchange) records to specify the mail server associated with a domain, making email communication possible.
- Performance Optimization: DNS enables efficient traffic routing, including balancing the load across multiple servers for high-traffic websites, improving web performance.
- Security Features: Modern DNS supports security protocols such as DNSSEC (DNS Security Extensions), which helps protect against DNS-related attacks like cache poisoning and man-in-the-middle attacks.
DNS Hierarchy
The DNS is structured hierarchically, starting from the root and moving down to specific domain names.
- Root DNS Servers: These are the top-level servers in the DNS hierarchy and are responsible for directing DNS queries to the appropriate TLD (Top-Level Domain) servers. There are 13 sets of root servers globally, which maintain the overall structure of the DNS system.
- Top-Level Domain (TLD) Servers: These servers handle the next part of the domain name, such as
.com,.org,.net,.edu, or country-specific domains like.uk,.in. TLD servers point to authoritative servers that hold the actual records for a domain. - Authoritative DNS Servers: These are the final servers that hold the actual DNS records for a domain. They are the ultimate source for resolving domain names into IP addresses. For example, if you are trying to access www.google.com, the authoritative DNS server for google.com will provide the IP address.
- Caching and Recursive DNS Servers:
- Recursive DNS Servers are intermediaries between the user and the authoritative DNS servers. They receive DNS queries from clients, perform the query resolution process, and return the results.
- Caching refers to storing previously queried domain name resolutions to speed up future lookups and reduce the overall load on the DNS infrastructure.
Types of DNS Records
DNS records are stored in authoritative DNS servers, and each type of record serves a specific purpose. Some common DNS record types include:
- A Record (Address Record): Maps a domain name to an IPv4 address.
- Example:
www.example.com → 192.0.2.1
- Example:
- AAAA Record: Similar to the A record but maps a domain name to an IPv6 address.
- Example:
www.example.com → 2001:db8::1
- Example:
- MX Record (Mail Exchange Record): Specifies the mail servers responsible for receiving email messages for a domain.
- Example:
example.com → mail.example.com
- Example:
- CNAME Record (Canonical Name Record): Used to alias one domain name to another. For example, a subdomain like
blog.example.comcan be aliased towww.example.com.- Example:
blog.example.com → www.example.com
- Example:
- NS Record (Name Server Record): Specifies which servers are authoritative for a given domain.
- Example:
example.com → ns1.example.com, ns2.example.com
- Example:
- PTR Record (Pointer Record): Used for reverse DNS lookups, where an IP address is mapped back to a domain name.
- Example:
192.0.2.1 → www.example.com
- Example:
2. Explain DNS lookup in detail with a case study. Discuss how DNS caching works and its impact on DNS resolution times.
DNS Lookup Process in Detail
DNS lookup refers to the process of translating a domain name into an IP address that computers use to locate services on the internet. Here’s how it works:
- User Query: When a user enters a URL like www.example.com in their browser, the browser sends a DNS query to resolve the domain to an IP address.
- DNS Resolver: The query is first sent to a DNS resolver, typically operated by the user’s Internet Service Provider (ISP). The resolver checks its cache to see if the IP address for the domain is already stored.
- Recursive Query: If the resolver does not have the record cached, it performs a recursive query by contacting the DNS root server, which directs the resolver to the appropriate TLD DNS server based on the domain extension (.com, .org, etc.).
- TLD and Authoritative Servers: The TLD server then refers the resolver to the authoritative DNS server for the domain (e.g., google.com). The authoritative DNS server holds the actual record and responds with the corresponding IP address.
- Response to User: The DNS resolver returns the IP address to the user’s browser, which can now connect to the correct web server and load the website.
DNS Caching and Its Impact
DNS Caching is the practice of storing DNS query results temporarily to reduce the need for repeated lookups and improve performance. Here’s how it works:
- Cache Storage: When a DNS resolver or a browser receives a DNS response, it stores the IP address in its cache for a predefined period (known as the Time To Live or TTL).
- Performance Boost: Cached results allow the resolver or browser to immediately use the stored IP address for future requests, reducing the time it takes to resolve the domain and reducing DNS traffic.
- TTL (Time to Live): The TTL value is set by the authoritative server and specifies how long the cached record remains valid. After the TTL expires, the record must be re-queried.
Impact of DNS Caching:
- Faster Resolution: Cached entries speed up future lookups as the system doesn’t need to query the authoritative servers every time.
- Reduced Load: By caching DNS records, the DNS resolver reduces the load on authoritative servers, contributing to faster internet performance.
- Potential Issues: Outdated or incorrect records may be cached, which can result in users being directed to incorrect websites. This is why TTL values are crucial in managing cache freshness.
Security Mechanisms in DNS
DNS is susceptible to various security vulnerabilities. To address these, security mechanisms like DNSSEC (DNS Security Extensions) have been implemented.
Common DNS Attacks
- DNS Spoofing/Cache Poisoning: In this attack, malicious actors inject false DNS records into the cache of a DNS resolver. This can lead to users being redirected to fraudulent websites.
- Example: A user may attempt to visit their bank’s website, but the cache poisoning attack redirects them to a phishing site designed to steal login credentials.
- DNS Amplification Attacks: Attackers exploit the DNS lookup process to amplify the size of a DDoS attack. By sending a small query to a DNS server with a forged source IP (the victim’s IP), they can generate large responses, overwhelming the victim’s network.
- Man-in-the-Middle Attacks: Attackers intercept DNS traffic between the client and the server, altering the data in transit.
3. Evaluate the security mechanisms in DNS. Discuss common DNS attacks such as DNS poisoning and how DNSSEC prevents such attacks.
How DNSSEC Prevents Attacks
DNSSEC (Domain Name System Security Extensions) adds a layer of security to DNS by ensuring the authenticity and integrity of DNS data. Here’s how it works:
- Digital Signatures: DNSSEC uses public-key cryptography to sign DNS records. This ensures that the data returned by a DNS server has not been tampered with during transmission.
- Authentication: DNSSEC allows resolvers to verify the authenticity of the response they receive from authoritative servers, preventing attacks like DNS spoofing.
- Chain of Trust: DNSSEC establishes a chain of trust from the root DNS server to the authoritative servers, ensuring that the data is valid from the top down.

